Zero-Trust Security Models Explained: An Overview to Explore Basics, Facts, and Key Insights
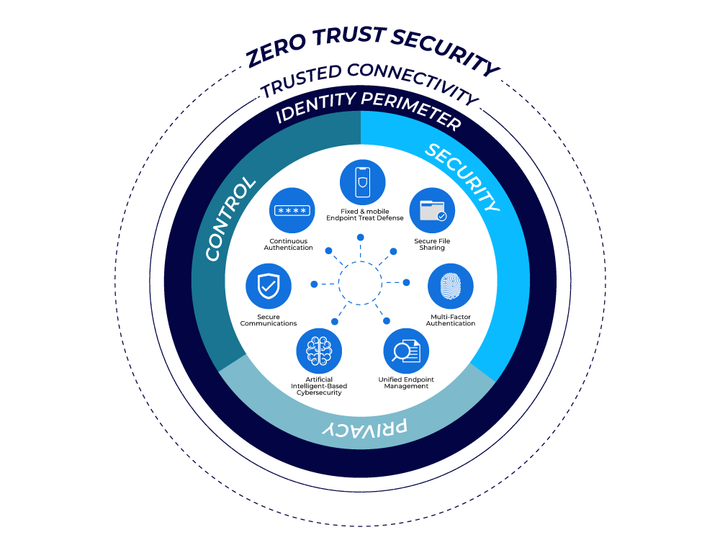
Zero-trust security models describe an approach to cybersecurity built on the idea that no user, device, or system should be trusted by default. Instead of assuming everything inside a network is safe, zero-trust treats every access request as potentially risky. Verification is required each time, regardless of location.
This concept exists because traditional network security relied heavily on perimeter defenses. Firewalls and internal networks were considered sufficient protection when most systems were located in one place. As organizations adopted cloud platforms, remote work, mobile devices, and interconnected applications, those assumptions became unreliable.
Zero-trust security models focus on identity verification, device health, and context. Access decisions depend on who is requesting access, what device is being used, and how sensitive the data is. The goal is not to eliminate trust entirely but to minimize implicit trust and replace it with continuous verification.
Why Zero-Trust Security Models Matter Today
Cybersecurity threats have become more complex and frequent. Data breaches, ransomware incidents, and unauthorized access attempts affect organizations of all sizes. Zero-trust security models matter because they directly address modern risk patterns.
These models affect a wide range of groups, including enterprises, public institutions, healthcare systems, educational organizations, and technology providers. Any environment handling sensitive data benefits from tighter access controls and better visibility.
Key problems addressed by zero-trust include:
-
Unauthorized access from compromised credentials
-
Insider threats, whether intentional or accidental
-
Limited visibility into user behavior
-
Overly broad access permissions
-
Difficulty securing cloud and remote environments
By applying least-privilege access and continuous authentication, zero-trust frameworks reduce the impact of breaches. Even if one account or device is compromised, attackers face barriers when attempting to move laterally.
Key Benefits Overview
| Security Challenge | Traditional Approach | Zero-Trust Approach |
|---|---|---|
| Network access | Trust inside perimeter | Verify every request |
| User permissions | Broad access roles | Least-privilege access |
| Device trust | Implicit device trust | Device posture checks |
| Threat response | Reactive controls | Continuous monitoring |
Recent Updates and Trends in Zero-Trust Security
Over the past year, zero-trust security models have continued to evolve alongside cloud adoption and regulatory pressure. Several notable trends emerged during 2024 and early 2025.
One major development has been the wider adoption of zero-trust architecture guidelines aligned with national cybersecurity strategies. Governments and large enterprises increasingly reference standardized frameworks rather than creating custom models.
Another trend involves stronger integration between identity systems and endpoint monitoring. Access decisions now rely more heavily on real-time signals such as device compliance, location anomalies, and behavior patterns.
Artificial intelligence and automation have also influenced zero-trust implementations. Behavioral analytics help detect unusual access patterns faster, while automated policy enforcement reduces response time.
Timeline of Notable Developments
| Date | Update or Trend |
|---|---|
| Early 2024 | Increased focus on identity-centric security |
| Mid 2024 | Growth in continuous authentication tools |
| Late 2024 | Expanded zero-trust guidance in public sector |
| Early 2025 | Deeper use of analytics for access decisions |
These updates reflect a shift from static security rules to adaptive, context-aware controls.
Laws, Policies, and Regulatory Influence
Zero-trust security models are influenced by national and international cybersecurity policies. In many countries, government guidance encourages organizations to move away from perimeter-based security and toward identity-driven frameworks.
In the United States, federal cybersecurity directives promote zero-trust architecture across government systems. Similar guidance exists in the European Union, where data protection and network security regulations emphasize access control, monitoring, and accountability.
India has also increased attention on cybersecurity governance through national digital security initiatives and sector-specific guidelines. While regulations may not mandate a specific architecture, zero-trust principles align closely with compliance goals such as data protection, auditability, and risk reduction.
Common regulatory themes connected to zero-trust include:
-
Strong identity verification
-
Controlled access to sensitive information
-
Continuous monitoring and logging
-
Reduced exposure of critical systems
Zero-trust security models help organizations demonstrate structured risk management without relying on outdated network assumptions.
Tools and Resources Supporting Zero-Trust Models
A variety of tools and resources support the practical application of zero-trust security models. These resources focus on identity, devices, networks, and data protection.
Key Tool Categories
-
Identity and access management platforms
-
Multi-factor authentication systems
-
Endpoint detection and response solutions
-
Network segmentation technologies
-
Security information and event monitoring dashboards
Reference Resources and Frameworks
| Resource Type | Purpose |
|---|---|
| Zero-trust architecture guides | Define principles and design patterns |
| Risk assessment templates | Identify access vulnerabilities |
| Policy mapping documents | Align controls with compliance |
| Monitoring dashboards | Visualize access activity |
Educational portals, technical documentation, and public cybersecurity frameworks provide structured guidance for understanding and applying zero-trust principles in real environments.
Frequently Asked Questions About Zero-Trust Security
What does “never trust, always verify” mean in practice?
It means every access request is checked before permission is granted. Identity, device status, and context are evaluated continuously rather than relying on prior approval.
Is zero-trust only relevant for large organizations?
No. While large enterprises often adopt formal frameworks, zero-trust concepts apply to any environment that handles sensitive data or remote access.
How does zero-trust differ from traditional network security?
Traditional models assume internal networks are safe. Zero-trust removes that assumption and applies verification equally to internal and external requests.
Does zero-trust eliminate cybersecurity risks?
It reduces risk but does not eliminate it entirely. Zero-trust limits damage by restricting access and improving visibility.
Is zero-trust a single product or technology?
No. It is a security strategy supported by multiple tools, policies, and processes working together.
Key Insights and Practical Understanding
Zero-trust security models represent a shift in mindset rather than a single technical change. They emphasize verification, visibility, and control at every stage of access. This approach aligns with how modern systems operate across cloud platforms, mobile devices, and distributed networks.
By focusing on identity, device health, and data sensitivity, zero-trust frameworks address the realities of today’s threat landscape. Continuous monitoring and adaptive policies help organizations respond to risk dynamically rather than relying on static defenses.
Conclusion
Zero-trust security models exist to address the limitations of traditional perimeter-based security. As digital environments become more complex, assumptions about trust create vulnerabilities. Zero-trust replaces those assumptions with structured verification and least-privilege access.
The importance of this approach continues to grow due to remote work, cloud computing, and evolving cyber threats. Recent updates show stronger alignment with national cybersecurity strategies and increased use of analytics for smarter access decisions.










